
How can strategic partnerships address the new cybersecurity threats to 5G networks?
The importance of 5G networks as critical infrastructure turns security into a principal requirement of the 5G network design. The new 5G Standalone (SA) architecture, designed for a wide range of application use-cases and connection of billions of devices, creates new security challenges and risks for the operator.
What are the cybersecurity risks in 5G?
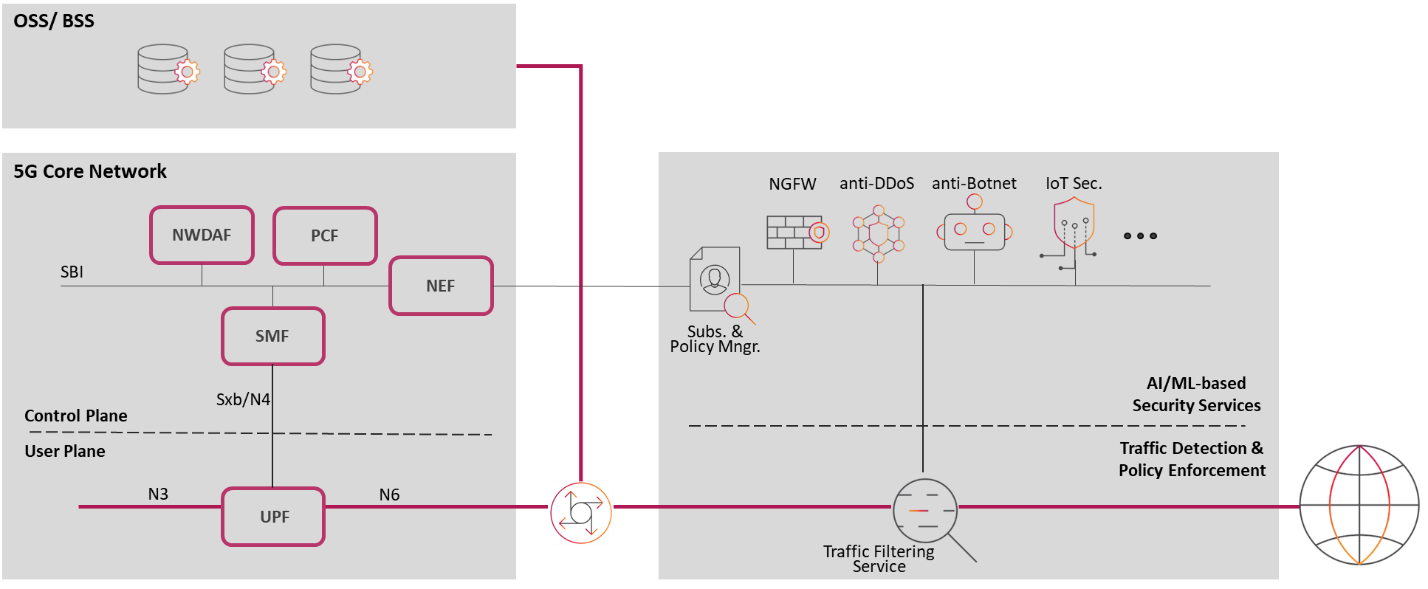
The interfaces between 5G networks and the public IP network – N6 interfaces, as defined by the 3rd Generation Partnership Project (3GPP) – pose specific security challenges to the service provider. The N6 interface carries data from the User Plane Function (UPF) to the Internet, performing a similar function as the S/Gi-LAN within a 4G network. It is also the point at which traffic travels across several essential network services, such as next-generation firewalls (NGFWs), distributed denial of service (DDoS) protection, traffic management, and IDS/IPS (intrusion detection systems / intrusion prevention systems).
The cloudified and distributed 5G architecture, with multiple MEC access points, increases security risk by creating more potential points of attack. Furthermore, we’re looking at 20x higher throughput per device, billions of connected IoT devices with no security standardization, and many new and futuristic use cases that require very low latency. Communication Service Providers (CSPs) who migrated or plan to migrate to 5G Standalone (SA) networks are already wrestling with these issues.
However, it’s not just Tier 1 and Tier 2 CSPs that wish to strategically avoid the specific security risks associated with 5G. 5G architecture also poses a cybersecurity threat to organizations of all sizes with large numbers of remote workers and distributed workforces spread across several regions. A significant portion of the market is seeking solutions to protect what amounts to a considerable number of potential attack vectors.
What type of solutions can address the 5G cybersecurity threats?
CSPs and organizations will be served best by an integrated solution that addresses the critical security needs of the service provider to protect the N6 interface between the 5G Core Network and the Public IP network.
Recommended solutions should simplify design, deployment, and operation of critical network edge functions. Additionally, the solution should have minimal impact on end-to-end latency.
To be effective, any solution must address specific criteria:
- Protection of the interface between the 5G Core Network and the Public IP network – the N6 interface as defined by 3GPP
- Automatic blocking of cyberattacks against CSP networks
- Blocking DDoS attacks that could overwhelm network functions and middle-boxes
- Smart load balancing to ensure scalability of the deployed stateless and stateful security functions and to simplify extension of the security services
- Ensuring sustained low-latency of networks to support high-value services.
No other method provides a comparable solution to address the comprehensive nature of this cybersecurity threat.
The framework for an ideal 5G cyberthreat protection solution
It’s worthwhile for cyberthreat solution providers to join in partnership to help communication service providers and others overcome key challenges in securing 5G networks. That way, they can work together to deliver the most secure, scalable, and integrated high-performance solutions to tackle this important issue.
The best solutions should combine at least two critical functions – next-generation firewall-based security and bi-directional DDoS protection on the N6. The list of security functions can be extended by including additional services (e.g., botnet isolation, IDS/IPS, WAF, etc.). A pre-integrated solution like this would offer the advantages of a multi-vendor, best-of-breed approach, with proven interoperability. It would also reduce the complexity of the 5G architecture by incorporating a tested solution that could simplify the design, deployment, and operation of critical network edge functions for the service provider.
In addition to N6 firewall and DDoS protection functionality, this type of solution could offer significant scaling abilities for the service provider’s network. Furthermore, this type of solution would have only one common in-line traffic filtering service, which is responsible for traffic monitoring, selective steering to the security services, and policy enforcement. This architecture allows parallel traffic inspection by different security functions and reduces end-to-end latency. This configuration enables improved utilization of security services, load protection in case of a network failure or volumetric DDoS attack, and dynamic resource allocation. A flow load balancer function could select for packets associated with a particular session, maintaining persistency, while reducing load on the security services.
In short, to mitigate the risk, a combination of the two major security functions of the user plane (firewall and anti-DDoS) into one comprehensive solution could provide volumetric DDoS protection and session-aware data-flow distribution for the virtualized NGFW, which should be able to deliver enhanced protection and reduced latency.
Are there other ways to gain similar 5G cyberthreat protection?
As it stands, the NGFW can be protected against volumetric DDoS attacks by any anti-DDoS product. However, high levels of integration, enabled through strategic solution provider partnerships, have the ability to foster the development of solutions that can scale automatically, with little to no service impact. These collaborative solutions also have the potential to significantly reduce TCO and improve competitiveness, especially in cloud-based deployments.
It’s worth noting that best-of-breed solutions of this type should be offered as pre-integrated multiservice security platforms, which would hopefully include automated multi-vector threat protection, QoS assurance for mission-critical apps, granular analytics, and forensics tools. It should probably be mentioned that, even in this case, the overall E2E latency will be calculated as a sum of latencies inserted by every security service deployed in-line (e.g., NGFW, IDS, IPS, WAF, ADC, etc.).
Considering the current state of 5G network roll out across the world, any solution should also support 5G non-standalone and 4G networks.
Partnership is the way to address the latest cybersecurity threats
Overall, vendor partnerships would help CSPs and other organizations to overcome key challenges in securing 5G and other networks by delivering the most secure, scalable, and integrated high-performance solutions to address today’s cybersecurity threats.
Regardless of the solution you choose, we’d be happy to talk more about it with you. By engaging on the issue and working together, we can increase the levels of partnership in the industry to address the latest cybersecurity threats to 5G and other networks.
FAQ
Specific risks involve N6 interfaces, defined by 3GPP, which carry data from User Plane Function (UPF) to the Internet.
Cloudified and distributed 5G architecture increases risks with multiple MEC access points and billions of IoT devices lacking security standardization.
Solutions should protect the N6 interface, automatically block cyberattacks, and prevent overwhelming DDoS attacks.
Smart load balancing for scalability and sustained low-latency support are essential features.
Partnerships enable the development of integrated solutions combining NGFW-based security and bi-directional DDoS protection.
These solutions simplify design, deployment, and operation of critical network edge functions while ensuring scalability and reduced latency.
Strategic partnerships can offer pre-integrated multiservice security platforms that automatically scale and reduce total cost of ownership (TCO).
Such solutions support various security functions, including automated multi-vector threat protection and QoS assurance for mission-critical applications, while addressing latency concerns.


