Are Complex and Targeted Floods Keeping You Up at Night?
In today’s dynamic business landscape, enterprises across all sectors are confronted with a formidable adversary: complex and targeted floods. These highly sophisticated flood attacks have been industrialized and weaponized to such an extent that they are even used by competitors. Their aim? To not only destabilize their counterparts’ network resilience, but also to threaten critical infrastructure, mission-critical services’ SLAs, and data security. These floods are not just a concern, they are a corporate crisis that demands immediate attention in an era when business continuity and digital uptime are paramount.
What are Complex and Targeted Floods?
Complex and targeted floods are a type of Distributed Denial of Service (DDoS) attack, which is far more advanced than traditional DDoS. These attacks employ a devastating combination of techniques to overwhelm target systems, including:
- Multi-Vector Attacks: Leveraging multiple attack vectors (TCP, UDP, HTTP etc.) simultaneously, to perpetrate the attack from multiple angles.
- Application-layer assaults: Leveraging specific protocols and services (e.g., DNS, SIP, ICMP) to exhaust the targeted server resources.
- Adaptive Payloads: Using unique, dynamic payloads designed to evade detection and mitigation, which are based on static pattern recognition.
- Botnet Orchestration: Harnessing a network of compromised devices (the “botnet”) to generate high-volume distributed traffic to overwhelm an attacked network.
Given their complexity, multi-vector attacks have become exponentially more difficult to detect and defend against, compared to standard volumetric DDoS attacks. However, this does not mean they are unbeatable. They can be overcome with a robust, multilayered security approach, empowering enterprises to stand strong against these threats.
The Escalating Threat Landscape
Complex and targeted floods are not just a menace, they pose a significant threat to enterprise network resilience. They have the potential to cause not only temporary disruptions but also open the floodgates to data breaches, malware infiltration, and even full-scale network shutdowns. This should be a cause for concern for all businesses.
These devastating attacks have been proven to:
- Harm business productivity and revenue.
- Damage brand reputation and customer trust.
- Incapacitate critical infrastructure like DNS, firewalls, and servers.
- Enable external attackers to exfiltrate sensitive information from the network.
With these threats’ escalating frequency and sophistication, enterprises can no longer rely on traditional DDoS defenses. As noted in the 2024 Report on the Cybersecurity Posture of the United States, “Malicious state and non-state actors are exploiting its seams with growing capability and strategic purpose, continuing to aggressively conduct malicious cyber activity that threatens U.S. national security, public safety, and economic prosperity.”
A New Approach to Defense
An innovative approach is needed: a multi-layered, service-aware protection to safeguard against complex and targeted floods. Additionally, Artificial Intelligence (AI) Neural Networks capabilities are highly recommended to support zero-day attack detection. The multilayered protection strategy should cover the entire network, from infrastructure to applications and services, and include:
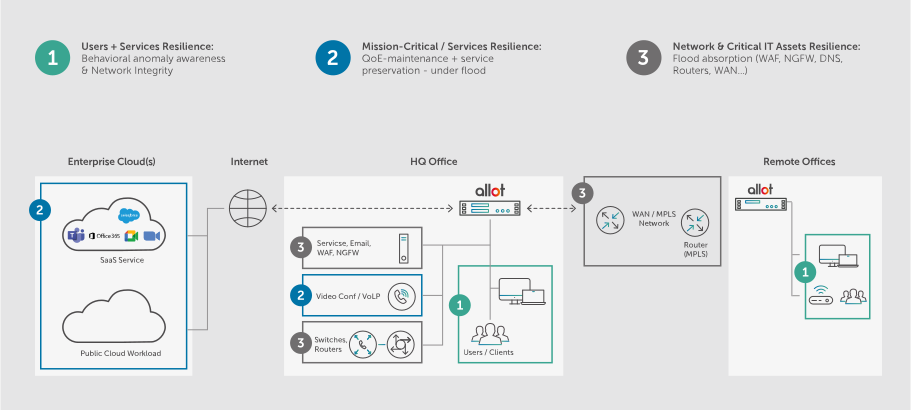
- Network and IT Asset Resilience: Inline protection with real-time anomaly detection and mitigation.
- User and Server Resilience: Rapid identification and remediation of botnet activity and command & control centers.
- Mission-Critical Service Resilience: Intelligent application classification and prioritization to ensure availability.
Moreover, to successfully deter multi-vector attacks, the ideal multi-layer protection system should provide corporate IT teams with a battery of combinable countermeasures, such as: anti-DDoS, anti-botnet, stateful firewall, and protect QoE under attack.
Implementing Advanced Solutions
By orchestrating these multilayered defenses and services, enterprise IT teams can rest assured that this comprehensive shield shelters them against the most sophisticated volumetric threats.
The Allot Network and Services Resilience (NSR) Solution
The Allot NSR Solution is a state-of-the-art multi-vector attack protection system. It offers AI-based zero-day detection, DPI-augmented anomaly awareness, and an instant mitigation solution. It utilizes a unique multi-level protection approach combined with high-scale machine-learning algorithms to achieve:
- Network & Critical IT Asset Resilience: Providing bidirectional volumetric and “bursty” Network Layer Anomaly Detection – NBAD (L3-L4), while ensuring critical services such as WAF and DNS are kept available, safe from volumetric floods. Mitigation can be executed within seconds, either on-premises, or within a cloud-based scrubbing center.
- User & Server Resilience: Automatically spots anomalous behavior of servers and endpoints. The system is also used to detect network infrastructure misconfigurations and can identify and mitigate botnet activities along with command-and-control (C&C) activities within just a few seconds. It then automatically isolates the infected endpoints to safeguard the network’s integrity.
- Mission-Critical/Services Resilience: By providing Intelligent application classification and applying the defined policy and prioritization to each application, this capability ensures the mandatory availability of mission-critical services. It also safeguards each application’s SLA under inbound and outbound floods and other anomalous behaviors.
The Allot NSR solution is trusted by leading worldwide Enterprises to empower their network and services resilience and ensure their business continuity.