Table of Contents
In an era of growing cyber threats, protecting the Communication Service Provider’s (CSP) services and revenue has become paramount. Recent industry research highlights telecom as the sector that was second most targeted by cyber threats in 2023, emphasizing the urgent need for robust security measures. This blog post explores the challenges mobile networks face in confronting cyber threats, and it advocates for a holistic approach to network protection.
The Growing Threat Landscape
Telecom networks face a dual threat – they are not only primary targets of attacks but also serve as conduits for malicious activities. Attacks orchestrated by bots, specifically IoT botnets, exploit weak devices, posing significant risks to critical infrastructure and services beyond the telecom domain. Volumetric inbound and outbound attacks, such as Fan-in DDoS, Fan-out, and Carpet Bomb, further expose telecom networks to threats that affect service availability, customer experience, revenue protection, sensitive data security, and the business resilience of the Communication Service Provider (CSP).
Growing access technologies such as fiber optic or 5G radio enable the generation of much more network traffic and enable the use of new applications. This leads to an increase in the number of threats that target the CSP and its customers. In addition, new encryption technologies make it difficult to detect malicious traffic and block access to suspicious Web resources.
The New Security Challenges
According to a recent IDC Technology Spotlight whitepaper, modern network technologies and a growing number of connected smart devices expose communication service providers to an expanding security attack surface. The diagram below illustrates the multitude of potential attack entry points, which include millions of poorly secured IoT devices.
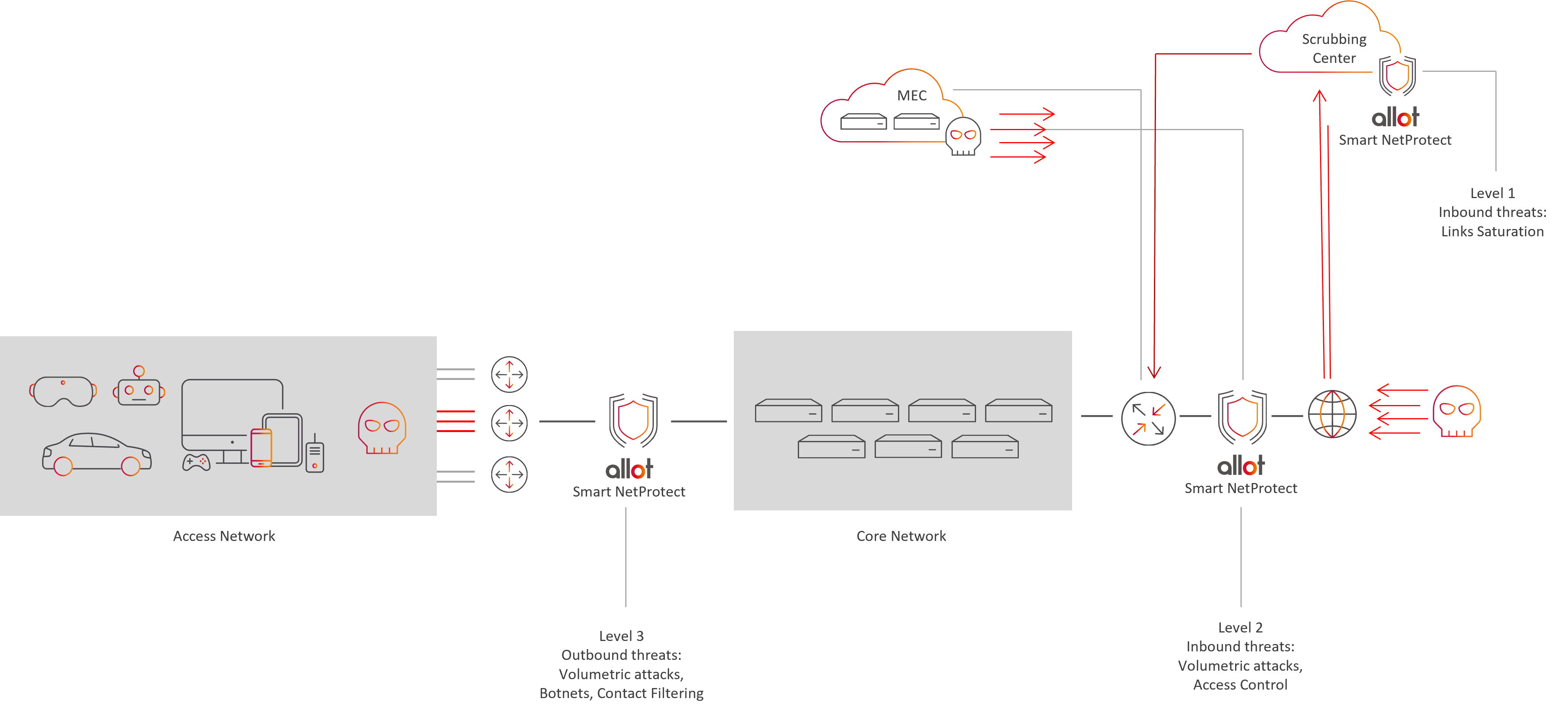
Tier-1, as well as Small and medium-sized service providers need inclusive network protection which is self-adaptive to traffic changes. Using machine learning to protect the network against zero-day/unknown attacks, the ideal solution combines several security services together (i.e., Anti-DDoS, anti-Botnet, Web-access control, and Firewall protection), provides an automated mode of operation to simplify operation, provides advanced threat forensics and analytics and protects QoE from degradation during attacks.
Traditional DDoS Mitigation Challenges
Traditional DDoS mitigation approaches, relying on flow-based statistical traffic sampling, face limitations in the context critical services and applications such as alarm systems and healthcare solutions. Flow statistics, while abundant, suffer from delays and reduced specificity, making them less effective against short, massive pulse attacks, which today account for more than 50% of attacks.
DPI-Based DDoS Mitigation: A Superior Solution
To address these challenges, DPI-based DDoS mitigation, based on deep packet inspection (DPI), emerges as a superior solution. Inline deep packet inspection allows for complete traffic captures without aggregation or sampling, offering granular and detailed information for faster and more accurate attack detection. The advantages of DPI-based mitigation include its ability to dynamically filter out attack traffic without impacting legitimate traffic, as well as providing quality forensics for real-time and post-attack analysis., all with significantly low Time-to-Response.
Integrating DPI-Based DDoS Mitigation with Next-Generation Firewalls
Technically, DPI-based DDoS mitigation and next-generation firewalls introduce a certain measure of end-to-end latency. This can become more pronounced when these functions occur separately on the network. To mitigate this, combining DPI-based DDoS mitigation with next-generation firewalls is proposed. This integrated approach combines traffic monitoring and threat detection functions, processing them in parallel to reduce latency. This one-pass approach not only preserves the low latency, but also allows functional expansion without additional latency risk.
The Added Value of DPI-based DDoS Mitigation
DPI-based anti-DDoS solutions, originally designed for subscriber traffic management, enable additional capabilities such as congestion management, application awareness, rate limiting, and advanced filtering. These capabilities make DPI-based solutions ideal for mitigating attacks and ensuring subscriber QoE during cyberattacks.
DPI-based Bot Recruitment Prevention
60% of attacks in telecom mobile networks are linked to Internet of Things (IoT) bots scanning for vulnerable hosts. Bots are a type of malware that searches for weak devices, a strategy connected with several IoT botnets. With billions of IoT devices around the world, ranging from smart refrigerators to smartwatches, many having poor security, cybercriminals have a wealth of targets to exploit. DPI-based anti-botnet protection provides host behavior analysis, detection of compromised hosts, threat intelligence, with detection of Command & Control (C&C) communication and automatic device/subscriber isolation. These capabilities prevent installation of attack launching pads, protect the CSP’s reputation and blacklisting of the network by peers.
Future-Proofing Telecom Network Security
In the face of evolving cyber threats, a combined firewall and inline DPI-based behavioral analysis emerges as a future-proof approach to efficiently protect CSP network services with automatic mitigation of known and unknown threats. This comprehensive solution offers protection against both inbound and outbound attacks, botnets, as well as advanced traffic management and detection capabilities to safeguard the performance of mission-critical applications during cyberattacks. The unification of user interfaces and shared functionality further contributes to an overall reduction in total cost of ownership for this combined, holistic security solution.
FAQ
Mobile networks face threats both as targets and conduits for cyberattacks.
Threats affect service availability, customer experience, revenue protection, and sensitive data security, impacting CSP business resilience.
Deep packet inspection (DPI) enables complete traffic captures without delays.
Offers granular attack detection and real-time analysis with low Time-to-Response.
Dynamically filters attack traffic without impacting legitimate traffic, ensuring quality forensics.
Combines DPI-based mitigation with next-generation firewalls to reduce end-to-end latency.
Parallel processing preserves low latency and allows functional expansion without additional latency risk.
Prevents bot recruitment by analyzing host behavior and detecting compromised hosts.
Provides automatic device/subscriber isolation and detects Command & Control (C&C) communication to protect CSP reputation and prevent network blacklisting.


 The growing wave of Phishing
The growing wave of Phishing FWA is coming! What you need to know
FWA is coming! What you need to know Prioritizing Small Business Network Security: A Call to Action for CSPs
Prioritizing Small Business Network Security: A Call to Action for CSPs


